How to Build your own Wi-Fi Deauther Device with Arduino
In this Arduino Hacking Tools guide, we are going to learn about internet packets, deauthentication attacks, and beacon spammers. Then we will make our own deauther device using a D1-Mini, Mini-OLED and some Push buttons. We are going to use Spacehuhn’s deauther code for this project. It is a beacon spammer, a packet monitor, and a deauther all rolled into one tidy project.
You can upload the code to an ESP8266 or ESP32 and easily control it using a web browser by logging into the network it creates. Another way is to add physical functionality to it using push buttons and a mini-OLED display.
What is an Internet Packet?
An internet packet, often simply referred to as a “packet,” is a fundamental unit of data that is transmitted over a computer network. These packets are used to convey information across the Internet and other networks, such as local area networks (LANs) and wide area networks (WANs). Packets are the building blocks of network communication, and they contain both the data being transmitted and control information necessary for routing and delivering the data to its destination.
What is a Packet Monitor?
A packet monitor, often referred to as a packet sniffer, is a software or hardware tool used for capturing and analyzing network traffic in the form of data packets as they traverse a network. Packet monitoring is a common practice in networking and cybersecurity for various purposes, including troubleshooting, network optimization, and security analysis.
Here’s how packet monitors work:
Capture Packets: Packet monitors intercept data packets as they flow through a network segment. These packets may contain various types of data, including web traffic, emails, application data, and more.
Analyze Packets: Once captured, the packets are analyzed to gain insights into network activity. This can include examining the source and destination addresses, protocol information, payload data, and more.
Packet monitoring serves several key purposes:
Network Troubleshooting: IT professionals use packet monitoring to diagnose network issues, identify bottlenecks, and determine the causes of network slowdowns or disruptions.
Security Analysis: Packet monitoring can help detect and analyze potential security threats, such as unauthorized access, malware, or suspicious network behavior.
Network Optimization: By studying network traffic, administrators can optimize network performance and bandwidth usage, improving the efficiency of data transfer.
Compliance and Auditing: In some cases, packet monitoring is used to ensure that networks and data are in compliance with legal and regulatory requirements. It can provide a record of network activity for auditing purposes.
Packet monitoring can be performed using various software tools and hardware devices, and it’s an essential component of network management and security in many organizations. However, it’s important to note that capturing and analyzing network packets may involve privacy and legal considerations, and it should be done in accordance with applicable laws and regulations. Unauthorized packet monitoring can violate privacy and legal rights.
What is a Deauther?
A “deauther” is a term commonly used in the context of Wi-Fi hacking and security. It refers to a device or software tool that is designed to perform deauthentication attacks on Wi-Fi networks. Deauthentication (often abbreviated as “deauth”) is a technique used to disconnect devices from a Wi-Fi network, essentially forcing them to reauthenticate and reestablish their connection. This can be done by sending deauthentication frames to specific devices or to the entire network.
Deauthers are typically used for a variety of purposes, including:
Security Testing: Cybersecurity professionals and ethical hackers may use deauthers to test the security of a Wi-Fi network. By disconnecting devices, they can assess how well the network handles such attacks and if it’s vulnerable to unauthorized access.
Penetration Testing: In penetration testing or “pen testing,” deauthers can be used to simulate real-world attacks and help organizations identify vulnerabilities in their Wi-Fi networks.
Network Troubleshooting: Deauth attacks can be used for legitimate purposes in diagnosing network connectivity issues. For example, it can be used to force devices to reauthenticate and establish a more stable connection.
Unauthorized Access: On the negative side, deauthers can be used by malicious actors to disrupt Wi-Fi networks, disconnect users, or even attempt to capture network credentials when devices reconnect.
Deauthentication Attacks
A deauthentication attack, often referred to as a “deauth attack,” is a type of cyberattack that disrupts or disconnects devices from a Wi-Fi network. This attack works by sending deauthentication frames (often abbreviated as “Deauth frames” or “Deauth packets”) to devices connected to a specific Wi-Fi network. When a device receives a deauthentication frame, it interprets it as a signal to disconnect from the network, even though the disconnection was not initiated by the user.
Here’s how a deauthentication attack typically works:
Identification: The attacker identifies the target Wi-Fi network they want to disrupt. This may be an open network or one with a known password.
Deauthentication Frames: The attacker sends a series of deauthentication frames to devices connected to the target network. Each deauthentication frame is addressed to a specific device, forcing that device to disconnect from the network.
Reconnection: After being disconnected, the affected devices will often automatically attempt to reconnect to the network. This can result in a cycle of disconnections and reconnections, effectively rendering the network unusable for legitimate users.
Deauthentication attacks can be carried out for various reasons, including:
Security Testing: Network administrators and security professionals may use deauthentication attacks as part of security testing to assess the network’s resilience to such attacks.
Unauthorized Access Prevention: It can be used to force unauthorized users or intruders off a Wi-Fi network to protect it from unauthorized access.
Malicious Intent: In some cases, attackers with malicious intent may use deauthentication attacks to disrupt Wi-Fi networks, causing inconvenience or attempting to exploit network vulnerabilities.
It’s important to note that conducting deauthentication attacks on Wi-Fi networks without proper authorization is generally illegal and unethical. Unauthorized deauth attacks can disrupt legitimate network users, and the attacker could face legal consequences. Responsible security testing and auditing should always be done with the appropriate permissions and within the boundaries of the law.
To defend against deauthentication attacks, network administrators can implement various security measures, such as using strong encryption protocols (e.g., WPA3), monitoring network traffic for suspicious activity, and employing intrusion detection systems.
What is a Beacon Spammer?
A “beacon spammer” is a device or software tool that is used to flood a Wi-Fi network with a large number of fake or malicious beacon frames. Beacon frames are a fundamental part of Wi-Fi network operation, as they are periodically broadcast by Wi-Fi access points to announce their presence and provide information about the network. These frames help devices discover and connect to available networks.
A beacon spammer generates and sends a high volume of malicious beacon frames, often with misleading or deceptive information, to disrupt the normal operation of Wi-Fi networks. The goals of beacon spamming can vary and may include:
Network Jamming: By overwhelming a network with excessive beacon frames, a beacon spammer can cause interference and make it difficult for legitimate devices to connect to the network.
Deceptive Networks: A beacon spammer can create fake access points (also known as “evil twin” networks) that mimic legitimate networks. This can be used to trick users into connecting to malicious networks, potentially leading to data theft or other security risks.
Network Enumeration: Beacon spamming can be used as a reconnaissance technique to gather information about Wi-Fi networks, such as the SSIDs (network names) of nearby networks, which may be useful for further attacks.
Disruption and Distraction: In some cases, beacon spamming may be used to create chaos or confusion, diverting attention and resources away from legitimate network operations.
It’s important to note that beacon spamming is generally considered a malicious activity and can be illegal in many jurisdictions. The use of such tools and techniques should only be employed by ethical hackers, security professionals, or network administrators for legitimate security testing, network analysis, or troubleshooting purposes, and always with proper authorization.
Defending against beacon spamming often involves implementing security measures such as intrusion detection systems, proper access point configuration, and monitoring for unusual or excessive beacon frames.
About Spacehuhn
“Spacehuhn” is a pseudonym used by a hacker and maker who has been known for various projects related to Wi-Fi security and electronics. Spacehuhn has gained recognition in the tech and hacker community for contributing to the development of open-source hardware and software tools. One of Spacehuhn’s notable contributions is in the field of Wi-Fi security and the creation of tools for testing and securing wireless networks.
One of the most well-known projects associated with Spacehuhn is the “esp8266_deauther,” which is a popular Wi-Fi deauthentication tool built around the ESP8266 microcontroller. This tool is used for security testing and allows users to perform deauthentication attacks, which can help identify vulnerabilities in Wi-Fi networks. It’s essential to note that deauthentication tools should be used responsibly and legally, with proper authorization and consent.
Spacehuhn has also worked on other projects related to electronics, programming, and cybersecurity. The online presence of Spacehuhn, including forums, blogs, and social media, has been a valuable resource for individuals interested in these areas.
It’s important to emphasize that while Spacehuhn has contributed to the open-source community with tools and resources related to Wi-Fi security, responsible and ethical usage of such tools is essential. Using them for unauthorized, malicious, or harmful activities is illegal and unethical. Always ensure that you have the necessary permissions and adhere to legal and ethical standards when using these tools for security testing or educational purposes.
Spacehuhn’s Deauther Project
The Spacehuhn Deauther project, often referred to as just “Deauther,” is an open-source software project created by a developer known as “Spacehuhn.” It is designed for microcontroller platforms, particularly the ESP8266 and ESP32, which are widely used for Internet of Things (IoT) and embedded projects. The project focuses on wireless security testing and auditing, specifically for Wi-Fi networks.
The primary feature of the Deauther project is the ability to perform deauthentication attacks on Wi-Fi networks. A deauthentication attack, often called a “deauth attack,” is a security testing technique used to disrupt or disconnect devices from a Wi-Fi network. It works by sending deauthentication frames to one or more devices connected to a particular Wi-Fi network, forcing them to disconnect from the network. This can be a useful security testing tool for network administrators and security researchers to identify potential vulnerabilities and weaknesses in their Wi-Fi networks.
Key features of the Spacehuhn Deauther project typically include:
Deauthentication Attacks: The project provides a user-friendly interface to initiate deauth attacks on Wi-Fi networks, helping users test the network’s ability to withstand such attacks.
SSID Scanning: It can scan for nearby Wi-Fi networks and display their SSIDs (Service Set Identifiers) and other information.
Captive Portal: Deauther can also create a captive portal, which is a web page that may pop up when users connect to an open Wi-Fi network. This can be used for various purposes, including displaying terms of service or collecting user data.
Beacon Frames: The tool can generate custom Wi-Fi beacon frames, allowing users to create their own Wi-Fi networks with specific characteristics.
OLED Display Support: Some versions of the Deauther project include support for OLED displays to provide a visual interface for scanning and deauth attacks.
It’s important to note that while the Spacehuhn Deauther project can be a valuable tool for security researchers and network administrators to test the resilience of their networks, it can also be misused for malicious purposes. Unauthorized deauthentication attacks on Wi-Fi networks are illegal in many jurisdictions and can have serious consequences. Therefore, it’s crucial to use such tools responsibly and only on networks for which you have explicit permission to conduct security testing.
The Code:
No code from me on this one, Spacehuhns project is amazing and way beyond anything I have ever written. You can download it here: https://github.com/SpacehuhnTech/esp8266_deauther
Deauther Without Buttons or Display
Spacehuhn’s Deauther project comes with a web-based user interface that allows you to configure and interact with the Deauther software. To log into a Deauther device, follow these general steps:
- Connect to the Deauther Device:
- Ensure that the Deauther device is powered on and its Wi-Fi network is available. On your computer or mobile device, search for available Wi-Fi networks. The Deauther device’s network SSID is
pwned.You can log into this network with the passworddeauther.
- Ensure that the Deauther device is powered on and its Wi-Fi network is available. On your computer or mobile device, search for available Wi-Fi networks. The Deauther device’s network SSID is
- Open a Web Browser:
- Open a web browser on your device (e.g., Chrome, Firefox, Safari) and navigate to a web address, typically “192.168.4.1” or “deauth.me.”
- Access the Web Interface:
- Once you enter the appropriate web address, you should access the web-based user interface of the Deauther project. You may need to provide a username and password. By default, the username and password are often set to “admin.”
- Configure and Use the Deauther Project:
- Once logged in, you can configure various settings, initiate deauthentication attacks, scan for Wi-Fi networks, and perform other functions available through the Deauther’s web interface.
Once you have successfully logged into the deauther, you will see a warning, which you will have to accept before proceeding.
To learn more about using the web interface you can read Spacehuhn’s tutorial here: Deauther Web Interface
Deauther With Buttons and Display
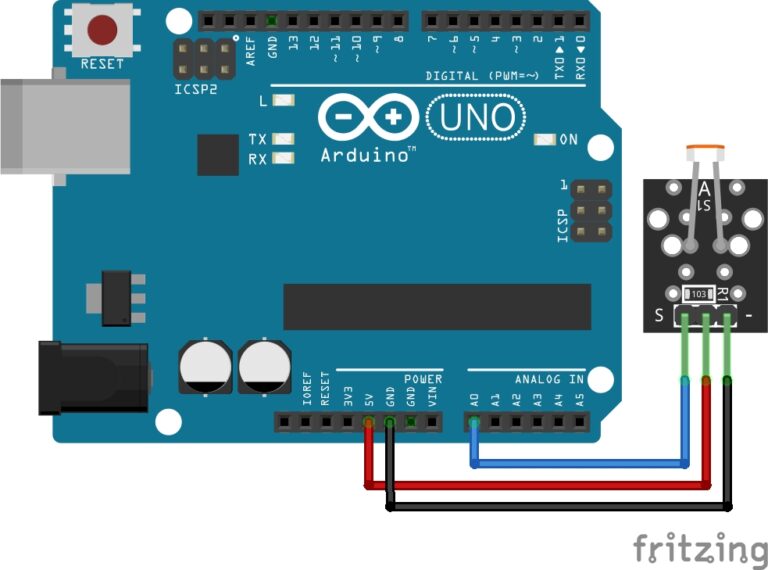
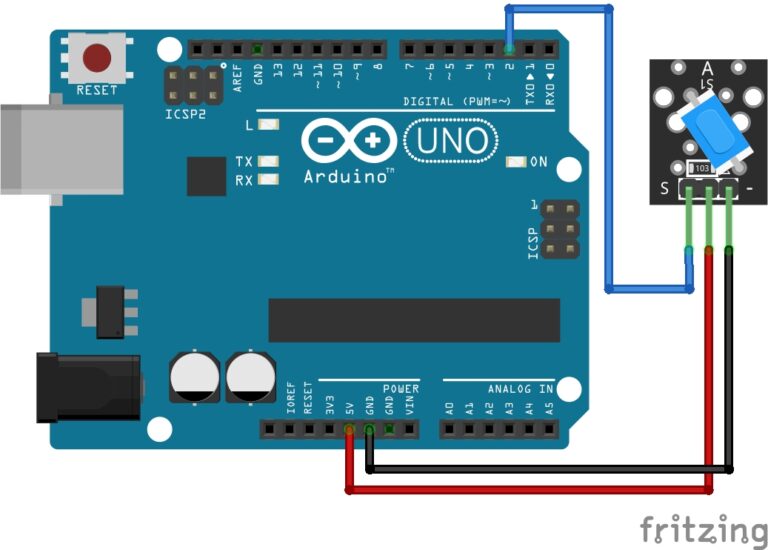
Components Needed:
The Circuit:
If you want to build a fully functional deauther device, complete with buttons and display, you can follow the circuit diagram below.

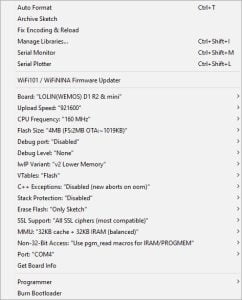
Upload the Code:
Below are the Arduino IDE board settings I used to successfully upload the code to the D1-Mini.
The Working Prototype

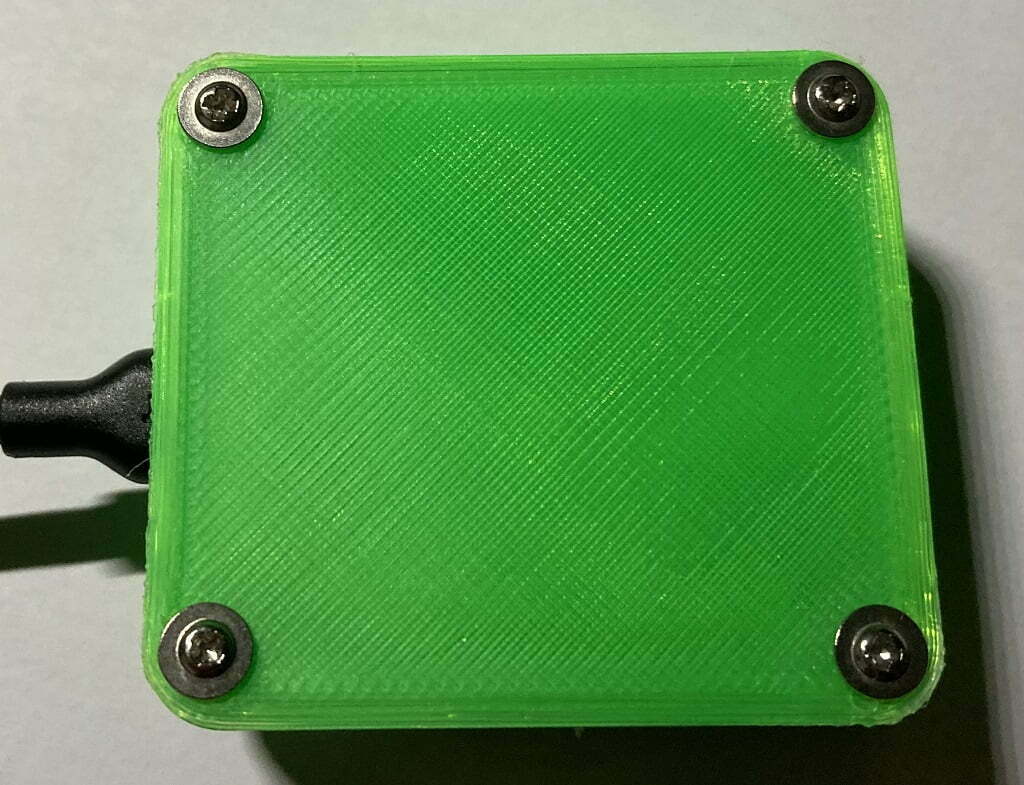
My Final Project
I went a step further and printed a case using my Ender3 printer. I got this pretty cool design from https://www.thingiverse.com/ it’s perfect for projects using the D1-mini and mini-OLED display.


Conclusion
This is a really great project created by Spacehuhn. It’s crucial to use Deauther or similar tools responsibly and only on networks for which you have explicit permission to conduct security testing. Unauthorized or malicious use of deauthentication attacks is illegal and unethical. Always adhere to applicable laws and ethical guidelines when using such tools.
Happy Hacking Folk’s!
Arduino Recommendations:
The Elegoo Super Starter Kit
If you don’t already own any Arduino hardware, we highly recommend this kit as it has everything you need to start programming with Arduino. You can find out more about this kit, including a list of its components here: Elegoo Super Starter Kit
You can find this kit on Amazon here: Elegoo Super Starter Kit
The 0.96-inch Mini-OLED Display
We highly recommend this mini-OLED bundle of five 0.96-inch OLED displays. We have bought these before and they all worked perfectly. You can read more about the mini-OLED here: Mini-OLED
You can find this bundle on Amazon here: OLED Displays
Elegoo Nano (Arduino Compatible)
We have bought these Nano boards many times and can highly recommend them. There are three Nano boards in this pack making them a total bargain for everyone.
You can find this pack on Amazon here: Arduino Nano
ESP8266 D1-Mini
D1-Mini is an Arduino compatible Wi-Fi board based on an ESP-8266-12F. This WLAN board has 9 digital I/O pins.
You can find this board on Amazon here: D1-Mini