
The Social Engineering App
In this Blackhat Python guide I will be talking about “The Social Engineering App”. It’s a password list generator used for dictionary attacks. I will explain in brief about password lists and dictionary attacks, but you can read my in-depth guide on these subjects here: Dictionary Attacks.
Passwords Lists
A password list, often referred to as a “password dictionary” or simply a “dictionary,” is a collection of words, phrases, or character combinations. Password lists are used for various purposes in the realm of cybersecurity, particularly in password-related activities. These lists can serve different functions, and their contents can vary, but their primary use is typically related to password security and authentication.
Dictionary Attacks
A dictionary attack is a type of cyberattack that involves systematically trying all the words or phrases in a predefined list (referred to as a “dictionary”) to gain unauthorized access to a system or online account. This attack is primarily used to crack passwords, and it relies on the assumption that many users choose weak or common passwords that are present in the dictionary.
What is The Social Engineering App?
If your password list for instance the rockyou.txt fails the dictionary attack, you can use this app to create a password list tailored to the target. People use passwords of things they remember whether it’s their favorite food, band, place, movie, person etc. We can gather this data using OSint tools like Facebook to create a custom password list. The original program generated over 2150 passwords for every keyword added, but now its smarter and creates thousands more.
The First Version
In the first version it was run from the terminal and took user input from the terminal. It was very basic but with every keyword inputted it would generate 2150 passwords.
The Second Version
The second version was given an interactive GUI and a few more parameters to create extra passwords. It looked good and worked well. You just keep submitting as many keywords you want and press quit to begin processing the password list.
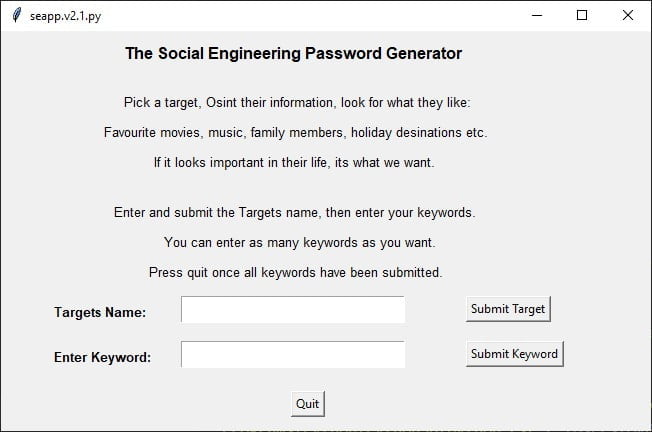
The Social Engineering App v2.1
This is the latest version of the app, and far more advanced than previous versions. The interface has had a huge makeover. I added many more LEET characters to increase the number of passwords for each keyword. Also, in the previous versions, they either had letters all in lowercase then all in uppercase, now it does all lower-case, all upper-case and will run through the keyword making one uppercase letter with the rest lowercase, cycling through 1 letter at a time. I included the add targets name function so the password list would be titled with the targets name.
It now has the ability to generate over 20,000 passwords for each keyword added.
The Code:
from tkinter import * from tkinter import messagebox import tkinter as tk import os
root=tk.Tk() root.geometry("650x400") root.title("seapp.v2.1.py")
def nameFile(): global fileName name=name_var.get() #Fetch Target name name_var.set("") fileName=str(name)+".txt" myFile=open(fileName,'w') #'w' Creates a clean file for generated passwords myFile.write('Your Generated Password List') myFile.close()
def submit(): #Pass generator main operations happen here myFile=open(fileName,'a') #'a' Appends each new keyword creation keyword=keyword_var.get() #Fetch User Input Variables keyword_var.set("") start=0 passRange=2150 myFile.write('\n') myFile.write(keyword) #regular myFile.write('\n') myFile.write(keyword.capitalize()) #capialize first letter myFile.write('\n') myFile.write(keyword.upper()) #uppercase myFile.write('\n') if keyword.__contains__('s'): #1337 starts here myFile.write(keyword.replace("s","$")) myFile.write('\n') if keyword.__contains__('a'): myFile.write(keyword.replace("a","@")) myFile.write('\n') if keyword.__contains__('e'): myFile.write(keyword.replace("e","3")) myFile.write('\n') if keyword.__contains__('i'): myFile.write(keyword.replace("i","1")) myFile.write('\n') if keyword.__contains__('t'): myFile.write(keyword.replace("t","7")) myFile.write('\n') if keyword.__contains__('o'): myFile.write(keyword.replace("o","0")) myFile.write('\n') if keyword.__contains__('s') or keyword.__contains__('a') or keyword.__contains__('e') or keyword.__contains__('i') or keyword.__contains__('t') or keyword.__contains__('o'): keyword=keyword.replace("s","$") keyword=keyword.replace("a","@") keyword=keyword.replace("e","3") keyword=keyword.replace("i","1") keyword=keyword.replace("t","7") keyword=keyword.replace("o","0") myFile.write(keyword) #leet myFile.write('\n') keyword=keyword.replace("$","s") keyword=keyword.replace("@","a") keyword=keyword.replace("3","e") keyword=keyword.replace("1","i") keyword=keyword.replace("7","t") keyword=keyword.replace("0","o") while start <= passRange: myFile.write(keyword + str(start)) myFile.write('\n') myFile.write(keyword.capitalize()+str(start)) myFile.write('\n') myFile.write(keyword.upper() + str(start)) myFile.write('\n') #1337 if keyword.__contains__('s'): myFile.write(keyword.replace("s","$")+str(start)) #leet myFile.write('\n') if keyword.__contains__('a'): myFile.write(keyword.replace("a","@")+str(start)) #leet myFile.write('\n') if keyword.__contains__('e'): myFile.write(keyword.replace("e","3")+str(start)) #leet myFile.write('\n') if keyword.__contains__('i'): myFile.write(keyword.replace("i","1")+str(start)) #leet myFile.write('\n') if keyword.__contains__('t'): myFile.write(keyword.replace("t","7")+str(start)) #leet myFile.write('\n') if keyword.__contains__('o'): myFile.write(keyword.replace("o","0")+str(start)) #leet myFile.write('\n') if keyword.__contains__('s') or keyword.__contains__('a') or keyword.__contains__('e') or keyword.__contains__('i') or keyword.__contains__('t') or keyword.__contains__('o'): keyword=keyword.replace("s","$") keyword=keyword.replace("a","@") keyword=keyword.replace("e","3") keyword=keyword.replace("i","1") keyword=keyword.replace("t","7") keyword=keyword.replace("o","0") myFile.write(keyword+str(start)) #leet myFile.write('\n') keyword=keyword.replace("$","s") keyword=keyword.replace("@","a") keyword=keyword.replace("3","e") keyword=keyword.replace("1","i") keyword=keyword.replace("7","t") keyword=keyword.replace("0","o") start=start+1 start=0 myFile.close()
def CLOSE(): myFile=open(fileName,'r') lines=len(myFile.readlines()) lines=lines-1 #we subtract 1 because of the welcome message at top of page print(lines) messagebox.showinfo("","SEAPP created " + str(lines) + " Passwords") root.destroy() name_var=StringVar() keyword_var=StringVar() title_label = Label(root, text = 'The Social Engineering Password Generator', font=('calibre',12,'bold')) desc_label1 = Label(root, text = 'Pick a target, Osint their information, look for what they like:', font=('calibre',10)) desc_label2 = Label(root, text = 'Favourite movies, music, family members, holiday desinations etc.', font=('calibre',10)) desc_label3 = Label(root, text = 'If it looks important in their life, its what we want.', font=('calibre',10)) guidePT1 = Label(root, text='Enter and submit the Targets name, then enter your keywords.', font=('calibre',10)) guidePT2 = Label(root, text = 'You can enter as many keywords as you want.', font=('calibre',10)) guidePT3 = Label(root, text='Press quit once all keywords have been submitted.', font=('calibre',10)) name_label = Label(root, text = 'Targets Name: ', font=('calibre',10, 'bold')) name_entry = Entry(root,textvariable = name_var, font=('calibre',15,'normal')) keyword_label = Label(root, text = 'Enter Keyword: ', font=('calibre',10, 'bold')) keyword_entry = Entry(root,textvariable = keyword_var, font=('calibre',15,'normal')) name_button=Button(root,text='Submit Target', command=nameFile) submit_button=Button(root,text='Submit Keyword', command=submit) close_button=Button(root, text="Quit", command=CLOSE) title_label.place(x=120,y=10) desc_label1.place(x=120,y=60) desc_label2.place(x=100,y=90) desc_label3.place(x=150,y=120) guidePT1.place(x=110,y=170) guidePT2.place(x=160,y=200) guidePT3.place(x=145,y=230) name_label.place(x=50,y=270) name_entry.place(x=180,y=265) name_button.place(x=465,y=265) keyword_label.place(x=50,y=315) keyword_entry.place(x=180,y=310) submit_button.place(x=465,y=310) close_button.place(x=290,y=360) #######################################################
tk.mainloop()
Conclusion
In the world of cybersecurity, having robust password lists for testing and analysis is essential. With our Python password list generator, you now have a powerful tool at your disposal. By inputting keywords, you can quickly generate extensive lists of passwords for security assessment, penetration testing, and beyond.
As we conclude this journey, remember that the effectiveness of such tools lies not only in their capabilities but in the responsible and ethical use of them. Utilize this newfound power wisely, respecting legal and ethical boundaries. Embrace the possibilities of enhancing your security practices and fortifying your defenses. Your commitment to learning and innovation is the key to staying one step ahead in the ever-evolving world of cybersecurity.
Happy Hacking Folks!
Read more of our Python guides here: Python Guides
Recommendations:
Basic Security Testing with Kali Linux: https://amzn.to/3S0t7Vq
ALFA Network Wi-Fi Adapter: https://amzn.to/3QbZ6AE
This Wi-Fi adapter is essential if you are to learn Wi-Fi Hacking.



